Enhancing cybersecurity in the cloud is crucial for protecting sensitive data from cyber threats. There are several strategies and solutions that organizations can implement to ensure robust data protection in the cloud. One key strategy is to implement strong access controls and encryption measures to secure data both at rest and in transit. Utilizing multi-factor authentication, role-based access controls, and encryption protocols can help prevent unauthorized access to data. Regularly updating security patches and conducting security audits are also essential for identifying and addressing vulnerabilities in cloud systems.
Multi-factor authentication (MFA):
Multiple forms of verification must be submitted by users before they can access sensitive data or systems, which adds an additional layer of protection known as multi-factor authentication (MFA). The process usually involves combining an identity such as a password, fingerprint, or face recognition. MFA significantly reduces the danger of unwanted access even in the event that credentials are compromised by requiring multiple factors for authentication.
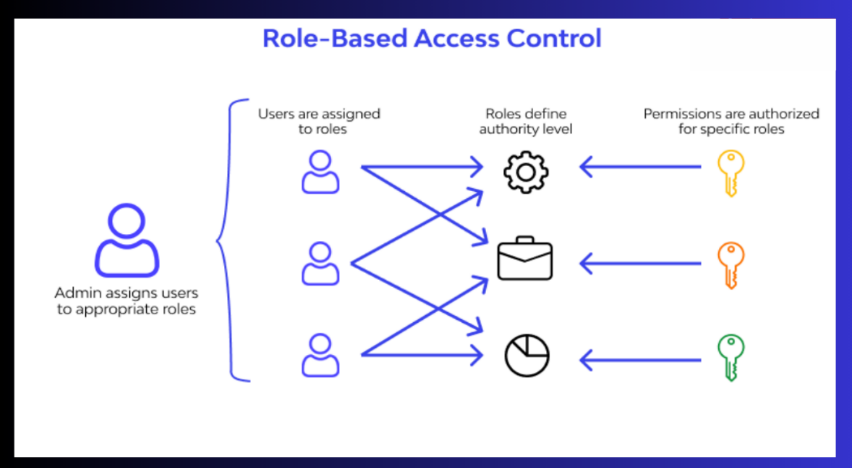
Role-based access controls (RBAC):
Role-based access controls restrict access to data and resources according to each user’s specific roles and responsibilities within the company. Access permissions are granted to users based on the unique role that they have been assigned.
For instance, a worker in human resources may only have access to personnel records, whereas a worker in the finance department may have access to financial data. RBAC reduces the possibility of unauthorized access to sensitive data by ensuring that users only have access to the information required for their job function.
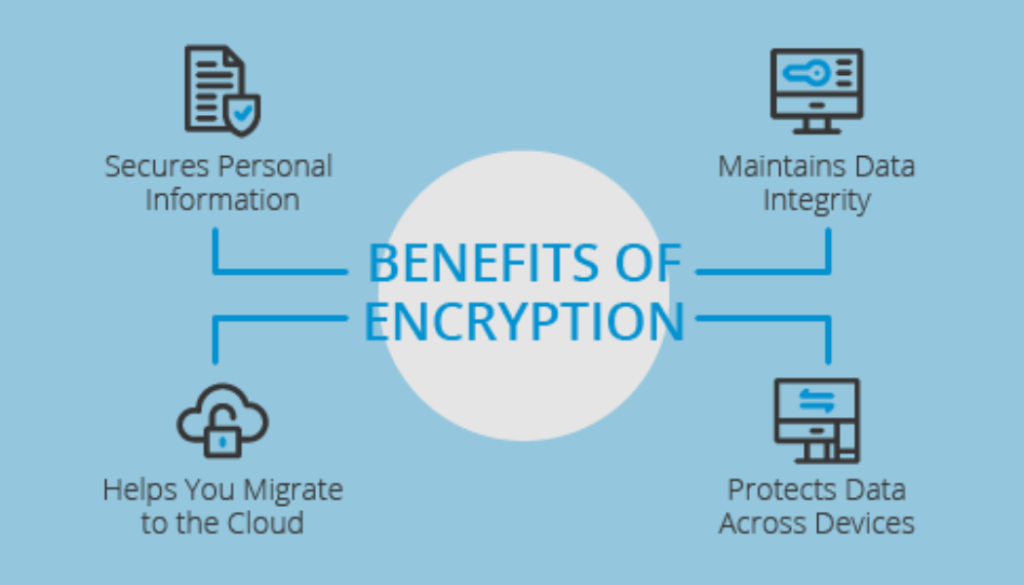
Encryption protocols:
Encryption protocols convert data into an encrypted form that is unreadable by unauthorized users and can only be decoded using the right decryption key. Organizations can safeguard sensitive information against interception and unauthorized access by encrypting data both in transit and at rest.
Additionally, organizations can benefit from using cloud security solutions such as Cloud Access Security Brokers (CASBs), Intrusion Detection and Prevention Systems (IDPS), and Security Information and Event Management (SIEM) tools. CASBs act as intermediaries between users and cloud service providers, providing extra security measures and insights into cloud usage.
IDPS monitors network traffic for indications of malicious behaviour, alerting security teams and preventing potential threats. SIEM tools offer centralized event tracking and incident reporting, empowering organizations to detect and respond to security incidents effectively.
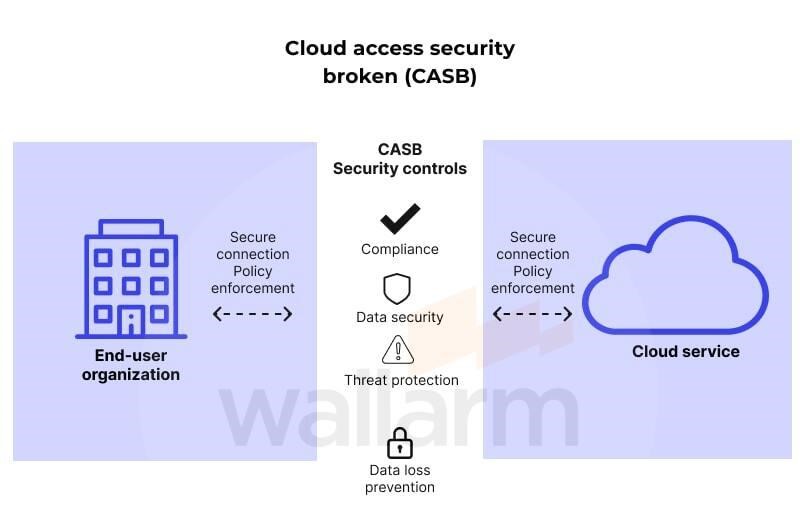
Cloud Access Security Brokers (CASBs)
Cloud Access Security Brokers (CASBs) specifically protect data and apps hosted in cloud settings. They ensure compliance with security policies and provide data encryption, access control, and threat detection capabilities, helping organizations maintain control over their data in cloud environments.
Intrusion Detection and Prevention Systems (IDPS)
Intrusion Detection and Prevention Systems (IDPS) monitor network traffic in real-time, identifying suspicious activity and notifying security teams. Some IDPS systems offer prevention features, automatically blocking or reducing threats before they cause damage, thus improving security and safeguarding critical information from online attacks.
Security Information and Event Management (SIEM)
Security Information and Event Management (SIEM) tools offer centralized event tracking, analysis, and reporting for security-related issues across an organization’s IT infrastructure. By correlating data from various sources, SIEM systems identify security threats and irregularities, empowering businesses to respond effectively and strengthen their cybersecurity posture in cloud environments.
By combining these strategies and solutions, organizations can enhance their cybersecurity posture in the cloud and mitigate the risks associated with storing data in cloud environments. Proactive measures and continuous monitoring are key to ensuring robust data protection and maintaining the integrity of sensitive information in the digital age.
![]()

